What’s 5/9/14 Eyes Surveillance Alliance? How do They Violate Your Privacy?

You should know something about the world’s biggest intelligence alliance groups – the Five Eyes, the Nine Eyes and the Fourteen Eyes, learn why and how they facilitate the worldwide surveillance.
It’s no secret that there are many intelligence alliances on the earth, among which the Five Eyes is taken as the team leader. A same name movie starring in Orson Fortune was scheduled to be on the theater screen in March 2022, but now this spy movie is renamed as Operation Fortune: Ruse de Guerre and the release date becomes “unspecified”. Maybe from this or other known blockbusters and episodes, we marvel at the fantastic and adventurous journey of the agents. However, the real world must be more risky and astonishing.
To help all of you understand better on the Five Eyes alliance and how it affects our online privacy and daily life, the following part will showcase members of the 5, 9 and 14 Eyes alliances, their histories, how they collect various intelligence information, as well as what we can do to keep away from the spying eyes.

What’s the Five/Nine/Fourteen Eyes Alliance?
Five Eyes, aka FVEY, is the most recognized and also the very first intelligence alliance among the anglosphere, whose history can be traced back to the World War II. All of the involved parties are bound by the multilateral agreement called The United Kingdom – United States of America/UKUSA Agreement[1].
Both Nine Eyes and Fourteen Eyes are expanded alliances of the Five Eyes, the latter of which is also known as SIGINT Seniors Europe/SSEUR, according to Snowden’s leaked documents from NSA.
Besides the three typical names, there are many other notorious intelligence arrangements such as Club of Berne, Maximator, The Counterterrorist Group, and NATO Special Committee, which are mainly intelligence-sharing groups consisting of different European nations.
There also go rumors or questions like will the Five Eyes become Four or Six Eyes and the US plans to invite India/South Korea/Japan/Germany/France to join the FVEY. Nevertheless, Five Eyes has been the Five Eyes for about 66 years.
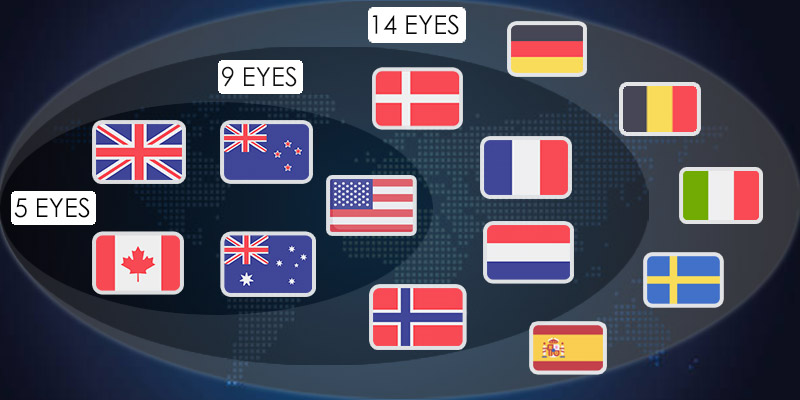
Who’re the Member Countries of the 5/9/14 Eyes?
Just as the names suggest, the Five Eyes, Nine Eyes and Fourteen Eyes alliances have the same number of member nations respectively.
- ☛Five Eyes Countries: the US, the UK, Canada, New Zealand, Australia
- ☛Nine Eyes Countries: The Five Eyes states + Denmark, France, the Netherlands, Norway
- ☛Fourteen Eyes Countries: The Nine Eyes states + Germany, Belgium, Italy, Sweden, Spain
History of the Five Eyes
As mentioned above, the Five Eyes Alliance originated during the Second World War and was initially an intelligence agreement just between the United Stated and the United Kingdom.
Although the very first proposal to establish an intelligence exchange mechanism between the US and UK was tabled in July, 1940, not until the breakout of Pearl Harbor attack in the next year did the United States be aware of the importance of intelligence exchange and sign the 1st intelligence agreement with the Great Britain, the primary purpose of which was to monitor the radios of the Axis powers/Rome-Berlin Axis. Specifically, the US monitored the Empire of Japan and the UK monitored Nazi Germany and the Kingdom of Italy.
Later on 17 May 1943, the BRUSA Agreement (Britain – United States of America agreement) came out to confirm their co-operation for detecting all foreign communication intelligence between the U.S. War Department and the British Government Code and Cypher School (GC&CS).
About 3 years later, another renewed UKUSA Agreement (United Kingdom – United States of America Agreement) was announced and enacted by the US and UK parties. This piece of agreement is commonly regarded as the foundation for signals intelligence cooperation between the two allies.
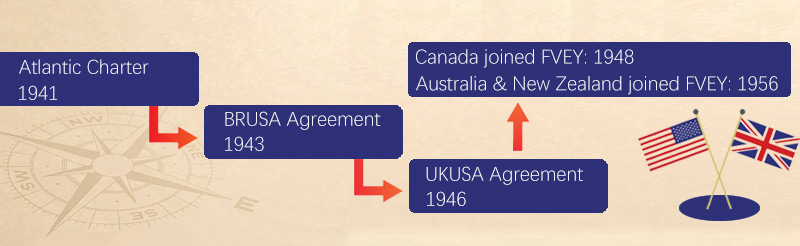
After that, three other countries – Canada, Australia, and New Zealand – joined the alliance successively in 1948 and 1956. That said, the Five Eyes Alliance was formed officially in 1956 and keeps the lineup to today. And they have very close cooperation during many historic events like the Cold War, the Vietnam War, the Falklands War, Gulf War and so forth, taking related interference measures to help things go as they expected, orchestrating assassinations of some political leaders or saving some dissidents from persecution.
How do 5/9/14 Eyes Nations Work for Intelligence Collection & Sharing?
There are multiple disciplines for intelligence gathering[2], and the 5/9/14 Eyes alliance adopts five of them roughly, say Signals intelligence (SIGINT), Human intelligence (HUMINT), Geospatial intelligence (GEOINT), Defence intelligence, and Security intelligence.
Set the Five Eyes for example, nearly all principle domestic organizations regarding intelligence, security, forces, and defense have joined the data gathering activities for further sharing. You can take a look at some typical agencies in the Five Eyes countries first:
| Five Eyes Alliance Country | Agencies Participated in |
| United States | CIA, FBI, NSA, DIA, and NGA |
| United Kingdom | DI, GCHQ, MI5, MI6, and SIS |
| Canada | CSE, CSIS, RCMP, and CFINTCOM |
| New Zealand | DDIS, GCSB, and GCSB |
| Australia | ASD, ASIO, ASIS, SGO, and DIO |
As a rule, each agency will focus on a specific type of intelligence like the NSA in charge of the signals intelligence concerning communication, electronic (voice or text) signals, telemetry data, etc, the FBI for security one, and the CIA for various human intelligence from all kinds of possible people. After they have collected the expected information publicly or secretly, they will arrange, analyze, and share it with member nations. Although it seems they only aim to watch other places outside the Five Eyes countries, the exposed NSA documents show that, regardless of the related domestic laws, those alliance members actually spy on their own citizens too. Big tech giants like Google, Yahoo, Apple, Microsoft, and MasterCard are all gathered by this alliance for more data collection.
Each country owns a different monitoring goal still. According to the PRISM materials revealed by Edward Snowden years ago, the US is mainly responsible for the areas of Russia, China, and Latin America, the UK for Europe and Africa, New Zealand for the South Pacific, Canada for Central and South America, Australia for the Asia regions including China, Malaysia, Thailand and so forth. Nobody knows whether there are any updates, however, one thing is for sure: the Five Eyes alliance has never stopped its surveillance.

Speaking of PRISIM, we have to come up with another code name – Upstream. Both PRISIM and Upstream are the Five Eyes Alliance’s information collection approaches from NSA, the former of which was started at 2007 and just aggregates user information from big tech companies located in or outside the US while the latter of which is said to have a really long history since 1972 and gets communication data from telephone and Internet straightforwardly via the fiber cables, switches, and infrastructure whenever there’re the (domestic or foreign) data flows. Beyond that, there are many other notable data gathering program names are revealed like say DANCINGOASIS, MOONLIGHTPATH, STATEROOM, and MUSCULAR. If you are interested, you can dig into them by extra googling.
The Five Eyes Alliance not only forces tech cooperation with many internet firms worldwide, but also seeks cooperation chances with other nations around the world, forming intelligence organizations like the Nine Eyes, the Fourteen Eyes, etc., and having states like Israel, Singapore, Japan, South Korea, and the British Overseas Territories be the close allies and assist the arrangement’s global surveillance continuously. If any target company or country doesn’t agree to join the data collection system, the Five Eyes Alliance’s government will probably impose certain sanctions on it, Yahoo, Huawei, a number of officials, just to name a few.
How the Five/Nine/Fourteen Eyes Alliance Affect Our Privacy?
Until now, we learn that two things are for sure:
– The 5, 9, 14 Eyes Alliances are trying to monitor and acquire all kinds of intelligence around the world, both their own citizen’s information and that from foreign places included.
– Their activities are supported by their own and also many other governments, even some of the behaviors violate relevant laws and human rights.
So what do you think about your privacy, especially web privacy? Nearly all popular tech giants from the western countries are members of the PRISIM system, your computer system provider, phone developer, internet service offers, financial institutions, what data you can imagine may be accessed, stored, and shared within the FVEY countries without hassle.
How to Protect Yourself Against Various Web Tracking, Surveillance, etc.?
The world of surveillance and censorship is complicated, and nobody can be the exception of this or that tight encirclement. In many circumstances, for an average user who want to safeguard their daily web browsing and online identity better, it’s suggest to make use of more secure internet services with advanced encryption methods, for instance secure encrypted email, messaging app, chatting app, private browsers, VoIP tools, virtual currency, as well as Virtual Private Network program.
The actual encryption way varies from service types and internal configurations maybe. But among all of those tools, only VPNs are able to secure all of your web traffic thanks to its unique VPN tunnel tech.
Here you can try PandaVPN to hide and change your IP address to another on in 80 countries and 170+ locations on the earth for upgraded privacy protection. But do remember to avoid those Five/Nine/Fourteen countries and regions where VPN is illegal or under government’s control.
Currently, a few heavily censored countries including Belarus, Iraq, North Korea, and Turkmenistan completely prohibit VPN use. Many more countries like China, Iran, Myanmar, UAE, and Russia tend to partially ban the usage of VPNs and only allow the VPNs that get the approval of governments. For more information to help you decide what VPN server to choose, you can visit our posts – Is VPN Legal or Illegal and Most & Least Censored Countries.

No-log policy also matters. If a VPN keeps user logs, there’s another chance of data breach, and the VPN provider may sell or hand it over to other parties for profit or other purposes. PandaVPN respects your privacy and won’t save any user log without your consent. Plus the first-in-class OpenVPN protocol (WireGuard will be supported soon), the highest level of ECC encryption, random digital account (email address is not a must-have), and BitCoin payment, you can trust this VPN to level up your online privacy and access the geo-blocked content.
External reading:
USUSA Agreement[wiki]
List of Intelligence Gathering Disciplines[wiki]
 Vic Knott
Vic Knott  2022.03.28
2022.03.28 











